Preamble
If you’re reading this, I have most likely already given a Ten Talk presentation at WLPC US 2026 in Phoenix, Arizona. With only ten minutes to present, the information I shared was limited. This blog is meant to provide more details on how we resolved this issue.
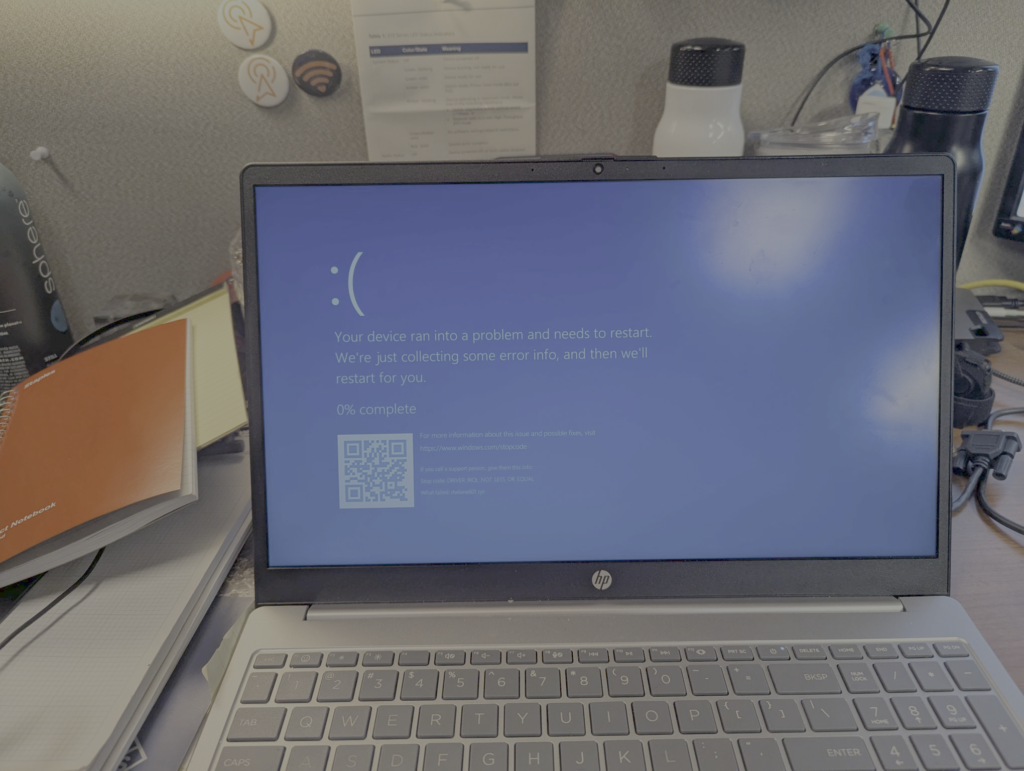
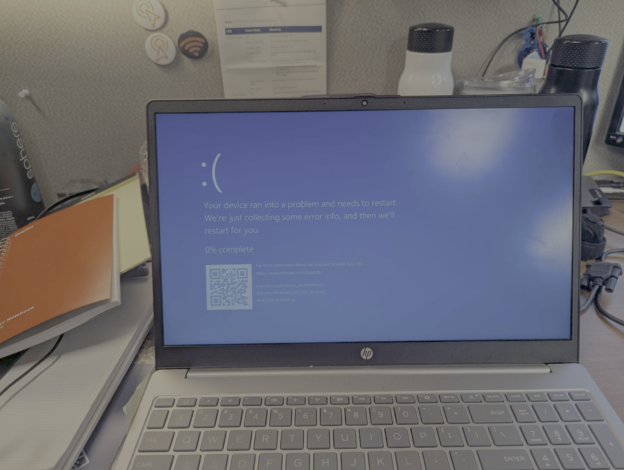
What would you do if you found out your Wi-Fi was essentially denial of servicing certain clients by causing them to crash? What if I told you this only impacted about 50 users total, approximately 0.001% of your client population? Would it change your level of concern or the amount of energy that you spent trying to solve this problem? Or would you tell those very few individuals to go away and get a new device? For me, every user’s experience matters and this is why I went through the process described in this blog to identify and resolve the issue (Windows laptops BSOD’ing) that was brought to me.
Continue reading